One of the biggest advantages of a Linux server is that you don’t actually need to be at the computer to use it. A Secure Shell (SSH) connection between computers can allow you to login remotely and operate command line functions from any computer – anywhere.
This is particularly useful if you’re starting to set up multiple machines but don’t necessarily have the space and peripherals to keep them all connected to their own monitors and cables. Switches can help manage multiple devices, but the simplest and cleanest set up will be to SSH in to whatever host machine needs to be accessed. As long as they’re all connected to the local network, the only wires required will be for the power supply, and the only peripheral we’ll need is a wireless network adapter. The Raspberry Pi even has one built in!
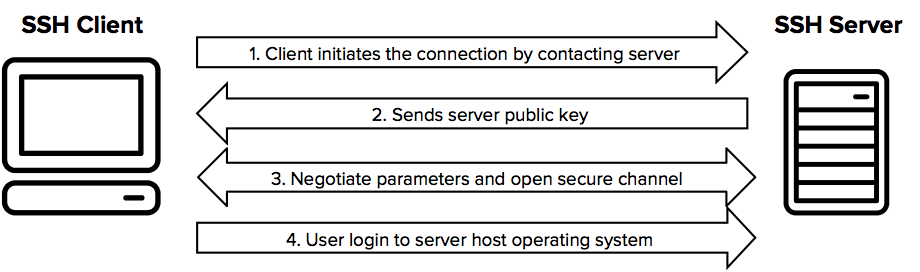
What is SSH?
SSH is short for Secured Shell, which is a protocol that typically runs on port 22. It’s been in use on Linux machines for a long time, but these days even Microsoft includes it (through OpenSSH installed by default in Windows 10). SSH allows you to log in remotely to any host computer that has the protocol enabled, and the encryption used ensures the connection is fully secured from pretty much everyone but the NSA.
The big advantage here is that the encryption allows you to log in securely as a user with root (or equivalent) access. Many SSH interfaces even let you transfer files directly to the server you’re connected to, so full administration can be handled remotely.
In many ways, SSH is a direct successor to the Telnet protocol. Both protocols allow command-line connections from remote users, but Telnet traditionally runs listening to port 23 and doesn’t support the encryption based security that SSH has. Otherwise, they’re very similar (although servers running Telnet protocols often had specific walled gardens set up for users to use rather than direct root access, due to said security limitations).
While Telnet is great for chat rooms and old BBS door games, it’s not necessarily the protocol you want to trust server security to: SSH is.
Installing SSH on a Raspberry Pi
Activating SSH on the latest Raspberry Pi is about as easy as it gets. The software comes pre-installed on the Raspbian distribution included with NOOBS, so we’ve really just got to enable it and configure it to get started:
- Enable WiFi (or ethernet) – The first step is to ensure that the Pi is connected to the local area network. This can be achieved by plugging in an active ethernet cable, or configuring the WiFi to log in to a remote access point. The WiFi can be enabled by clicking on the WiFi icon in the upper right corner of the screen and typing in the passcode. Super simple.
- Enable SSH – SSH can also be enabled through the desktop interface by clicking Preferences ->
Raspberry Pi Configuration -> Interfaces and then selecting ‘Enabled’ next to the SSH option. This can also be achieved from the command line by typing:sudo systemctl enable ssh sudo systemctl start ssh - Log in – Get an SSH client for whatever desktop you’re using as a terminal. I like MobaXterm because it supports so much more than just SSH. The SFTP interface allows you to easily transfer and edit files while keeping the command line access open, and that’s pretty much like having full control over a PC without dedicating a monitor, keyboard, or mouse to do so.
Notes on Security
By default, SSH on a Pi won’t enable root user access remotely. This is something you can change within the configuration file found at /etc/ssh/sshd_config
Find the line PermitRootLogin without-password and edit it to say PermitRootLogin yes
After that, save up the file and reboot the system (or restart SSH).
Please note: This is generally not necessary, nor is it usually advised. Most required commands can be issued using sudo, but this can be an alternative method of full control if you set up a strong password and force SSH keys.

Leave a Reply